

Akamai: WAAP and DNS Solutions for High-Level Web Security
Protect Your Infrastructure with the Power of Akamai's WAAP and DNS Solutions

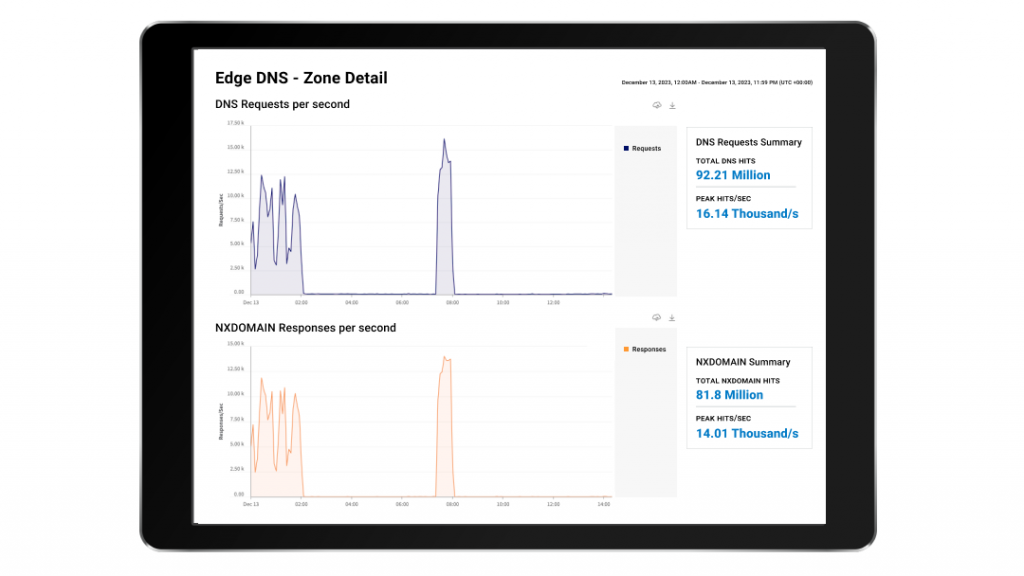
Achieve Unmatched Security, Performance, and Availability with Akamai Edge DNS
Rely on a highly scalable and flexible DNS security solution that provides:
- Comprehensive Security. Protect your DNS infrastructure against increasingly large, frequent, and sophisticated attacks, whether in the cloud, on-premises, or in hybrid environments.
- Unmatched Performance. Leverage the world’s most distributed platform to offload origin traffic, ensure 24/7 availability, and reduce page load times.
- Intuitive Management. Automatically configure and manage your DNS zones, and apply your own dynamic policies in real time.
Enhance the security and performance of your DNS using our powerful edge platform.
Ensure uninterrupted DNS availability.
Protect your on-premises and hybrid DNS assets
Achieve peace of mind with secondary DNS
How Edge DNS works
CONFIGURE
CONFIGURE
Customize your primary and secondary DNS zones through APIs or tools like Terraform, via the Akamai Control Center.
PROTECT
PROTECT
Leverage optional DNSSEC features to prevent attacks caused by DNS spoofing.
DEPLOY
DEPLOY
Provision, delegate, and update your zones, whether in the cloud or on-premises, via the Akamai Control Center to get up and running.
Protect Your On-Premises and Hybrid DNS Infrastructure
Akamai Shield NS53 is a reverse proxy solution designed to safeguard on-premises and hybrid DNS infrastructures, including GSLBs, firewalls, and name servers, against resource exhaustion attacks. Clients can self-configure, manage, and enforce their own dynamic policies in real-time.

Mitigate NXDOMAIN DNS Queries at the Edge
Protect your DNS infrastructure from NXDOMAIN attacks in real-time with dynamic, self-configurable security policies.

Enjoy Flexibility and Ease of Use
Self-configure and manage your security policies, rate controls, APIs, and zone transfers with an intuitive and user-friendly interface.

Boost Performance with Global Anycast
Reduce latency and enhance user experience with cached responses, global IP anycast, and the NAMES network offered by Akamai.
WAAP Solutions
WAAP solutions provide protection against growing threats.
WAAP stands for Web Application and API Protection, a class of security technologies designed to safeguard web applications and APIs from increasingly sophisticated cyberattacks.
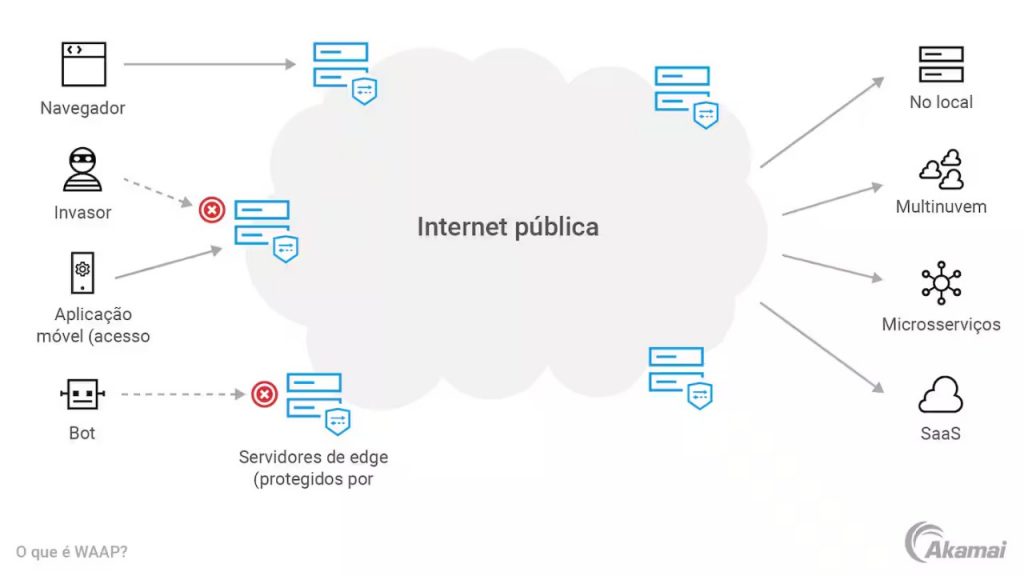
Enhanced Security for Applications and APIs with Less Effort
Adapt Defenses to the Latest Threats
Automate Updates and Self-Tuning for Simplified Security
Empower Developers and Security Teams
How the App & API Protector Works
DIRECTION
DIRECTION
A core technology, the Adaptive Security Engine, learns attack patterns and adapts to emerging cybersecurity threats.
DEFENSE
DEFENSE
All requests are inspected in real-time to protect against DDoS attacks, web application and API threats, and malicious bots.
ADAPTATION
ADAPTATION
The automated defense of the Behavioral DDoS Engine safeguards your organization from sophisticated volumetric attacks.

Features
Get to know it now and understand the real reasons why you should buy this product!
- Adaptive protections automatically deploy the latest defenses for applications and APIs, including zero-day and CVE protections.
- Proactive self-tuning eliminates the time-consuming manual patching of security vulnerabilities in web services.
- DDoS protection blocks network attacks at the edge and defends against application-layer threats, enabling secure and rapid web application innovation.
DDoS Protection
Robust, behavioral DDoS defense for all layers—whether in the cloud, on-premises, or within hybrid architectures.
Defend Against Modern, Sophisticated Attacks
Today’s businesses face the constant threat of sophisticated and well-orchestrated DDoS attacks. Akamai’s DDoS protection, built on dedicated infrastructure, safeguards your internet-facing applications and systems while ensuring a fast, highly secure, and always-available DNS.
With Akamai, you can stop DDoS attacks and malicious traffic in the cloud before they reach your applications, data centers, and infrastructure—without relying on multiple firewalls.
Enhance Security for Applications and APIs with Less Effort

Ensure Business Continuity
Operate with confidence, knowing your DDoS defense is backed by dedicated infrastructure.

Optimize Protection for Your Use Cases
Maintain a fast, always-available DNS with segmented resources in non-overlapping clouds.

Gain Full Control Over Traffic Before It Reaches Your Servers
Stop attacks in the cloud and free up internal resources.
Akamai Guardicore Segmentation
Eliminate Network Risks with Industry-Leading Micro-Segmentation
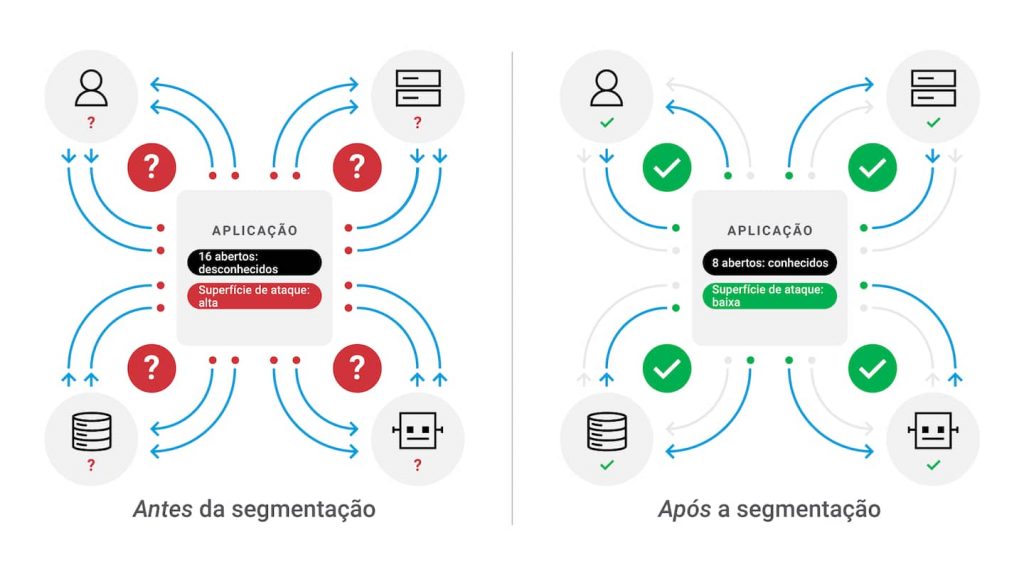
Prevent Lateral Movement with Granular Controls
Safeguard your organization’s critical assets with Akamai Guardicore Segmentation.
- Fast. Utilizes software-based segmentation to prevent attackers from accessing your most sensitive information, outperforming slower infrastructure-based approaches.
- Simple. Easy to deploy and manage, empowering IT teams with the visibility and control needed to apply Zero Trust principles across data centers, multi-clouds, and endpoints.
- Intuitive. Blocks malicious lateral movement within your network by enforcing precise segmentation policies based on comprehensive visual insights of your environment.
A Better Way to Achieve Zero Trust Segmentation
Reduce Your Attack Surface
Prevent Lateral Movement
Protect Critical IT Assets
How Akamai Guardicore Segmentation Works
MAPPING
MAPPING
Sensors, data collectors, and logs map your network to provide a unified view of assets and infrastructure.
CREATE
CREATE
Simplify security policy creation with predefined templates and workflows, with no limitations on allow/deny rules.
VIEW
VIEW
View past or real-time activity at the user and process level to quickly identify potential violations.

Features
ResourcesDiscover now and understand the real reasons why you should buy this product!
- Granular micro-segmentation down to individual processes and services.
- Simplified forensic analysis with near real-time and historical visibility.
- Broadest platform coverage for both legacy technology and modern systems.
- Customized threat-hunting services powered by Akamai Security Research.
Contact
One of our experts will contact you as soon as possible!
Send us your contact details. All your data will be safe and we’ll take good care of it.